The Linux Logical Volume Manager The second generation of the Linux Logical Volume Manager (LVM2) is a logical volume manager c...
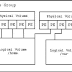

The Linux Logical Volume Manager The second generation of the Linux Logical Volume Manager (LVM2) is a logical volume manager c...

Step 1. BIOS (Basic Input Out System) System power on, hardware transfer control to BIOS . BIOS is the first program to run and it’s...

1. Introduction Endian Firewall is a Unified Threat Management (UTM) Appliance that protects networks and improves connectivity. Base...

This past week, two important updates were issued for PHP, providing both security and bug fixes. Like many things in the open-source ...
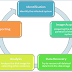
Introduction: A digital forensic investigation generally consists of five major steps [Figure-1]: Identification Data Acquisition ...

1. Introduction DenyHosts is an open source and free log-based intrusion prevention security program for SSH servers developed...

1. Introduction ClamAV is an open source (GPL) antivirus engine designed for detecting Trojans, viruses, malware and other malicious th...

1. What is Malware? Malware is called malicious software, script or code which is created and used by hackers to retrieve informa...

1. Introduction Runlevels define what services or processes should be running on the system. The Linux operating system can make use of...

#!/bin/bash # Under RedHat / Centos if [ $# -gt 0 ] then MIN=$1 else MIN=8 fi DEL=`expr $RANDOM % 5` LEN=`expr $MIN + $DEL` cat /dev/ur...

1. Overview rkhunter (Rootkit Hunter) is a Unix-based tool that scans for rootkits, backdoors and possible local exploits. It does...

1. Linux Command Line Linux Reference Card – Great reference published on FOSSwire website One page Linux Manual – Great one page ...
1.Introduction Lynis is a free and open source auditing tool for Unix-based operating system. It will provide report and makes suggest...

By default the Linux OS has a very efficient memory management process that should be freeing any cached memory on the machine that it ...